0x01 Requirements
Recently, several projects started due to clients being attacked by ransomware. To quickly understand which clients have been disclosed by ransomware groups on the dark web, what the situation is, how much data has been leaked, and which organizations are involved, we considered monitoring the main pages of common ransomware groups on the dark web to gather this information.
After conducting some technical research, I found a few websites that provide consolidated information, along with the source code:
Website: https://www.ransomlook.io/
Source code information:
The public service provided by the website meets my needs, and since I don’t require very high real-time monitoring, simply tracking the website is the best choice.
0x02 Setting Up Quickly with n8n
Monitoring a website and obtaining the necessary information can be done in many ways as long as the site does not have anti-scraping measures. Since I’ve already deployed the n8n software, developing a workflow using this mature software is the easiest approach.
Without going into detail for each component, the final workflow looks like the image below for reference:
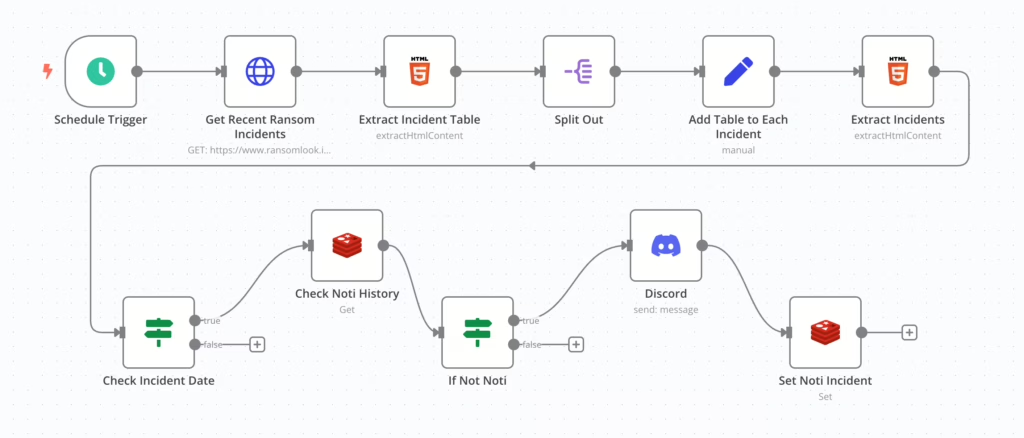
In this workflow, the specific challenges encountered are documented in the second Extract Incident function. The recorded information is as follows:
Captured Event Details
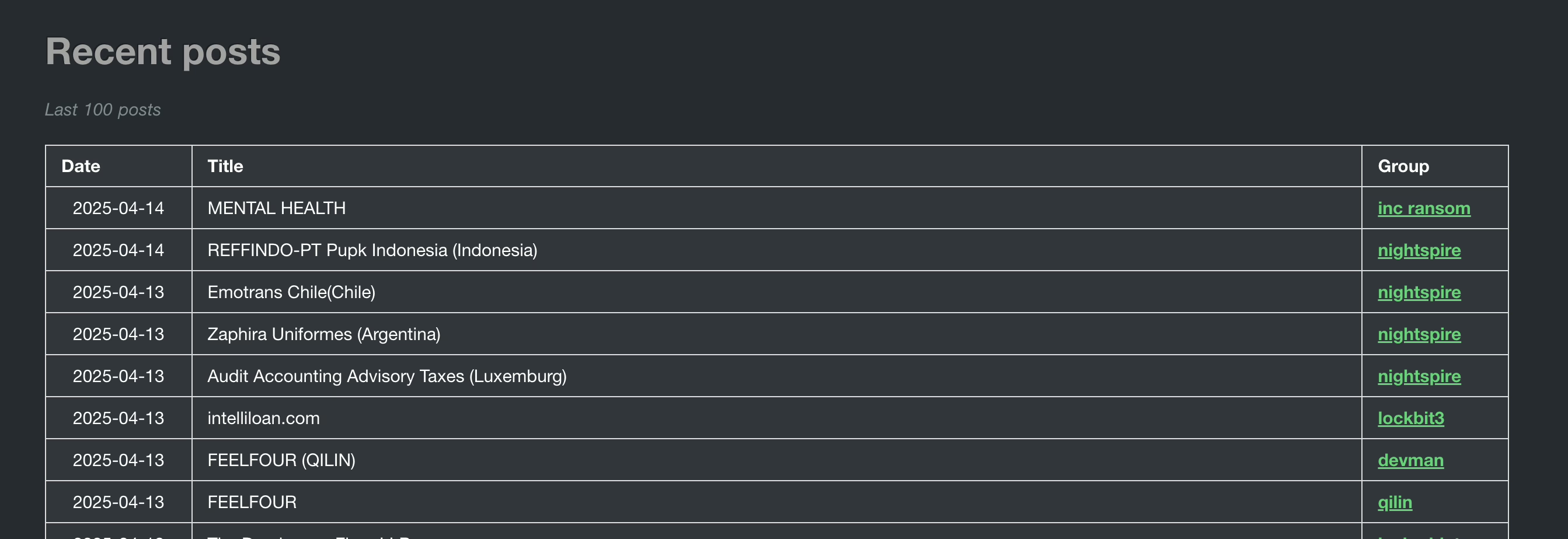
The recent feature on the website provides a <table> that displays the last 100 ransomware incidents, with each row formatted as follows (for clarity, I removed the outer table/tr/td tags):
<td><center> 2025-04-14 </center></td><td> MENTAL HEALTH </td><td> <a href="/group/inc ransom">inc ransom</a></td>",
"<td><center> 2025-04-14 </center></td><td> REFFINDO-PT Pupk Indonesia (Indonesia) </td><td> <a href="/group/nightspire">nightspire</a></td>Points to Note
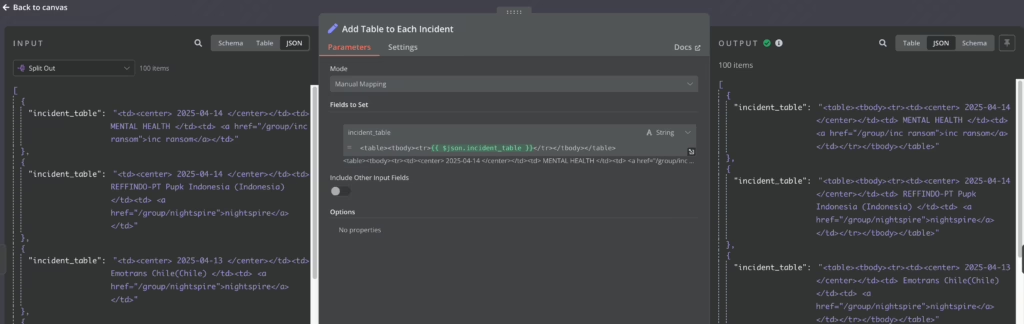
After retrieving the content of this table, I naturally used the td tag to gather explanations for each event, but I discovered that I couldn’t retrieve the corresponding content in n8n. After checking the official community, I confirmed that this issue arose because this particular code snippet doesn’t form valid HTML. Therefore, I added a component to complete this HTML fragment into a standard analyzable format:
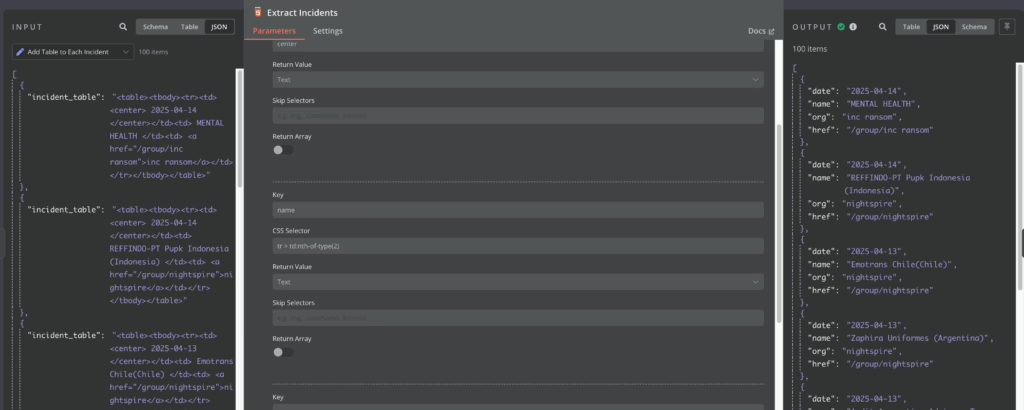
After completion, the subsequent code nodes can properly retrieve the content and assemble it:
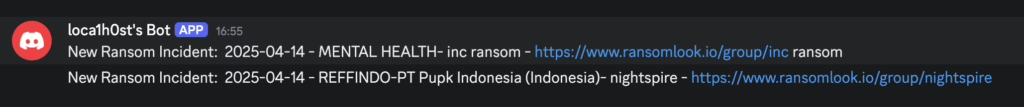
Final Outcome
I set up a scheduled task to run every hour, which sends notifications to a Discord channel whenever an event is detected:
0x03 Example of Using AI
After taking so much time on this, it turns out that analyzing HTML or even the entire process can be accomplished with a simple AI prompt. Without worrying about costs, I highly recommend using AI to perform this task as it saves a lot of time…
Leave a Reply