Background
Today, while scrolling through my social media feed, I noticed a friend initiated a “Harmony Challenge” using a third-party app, where a successful challenge earns you a milk tea voucher. Clearly, as a close friend who grew up together, I had to ace this challenge.
Overview of the Business
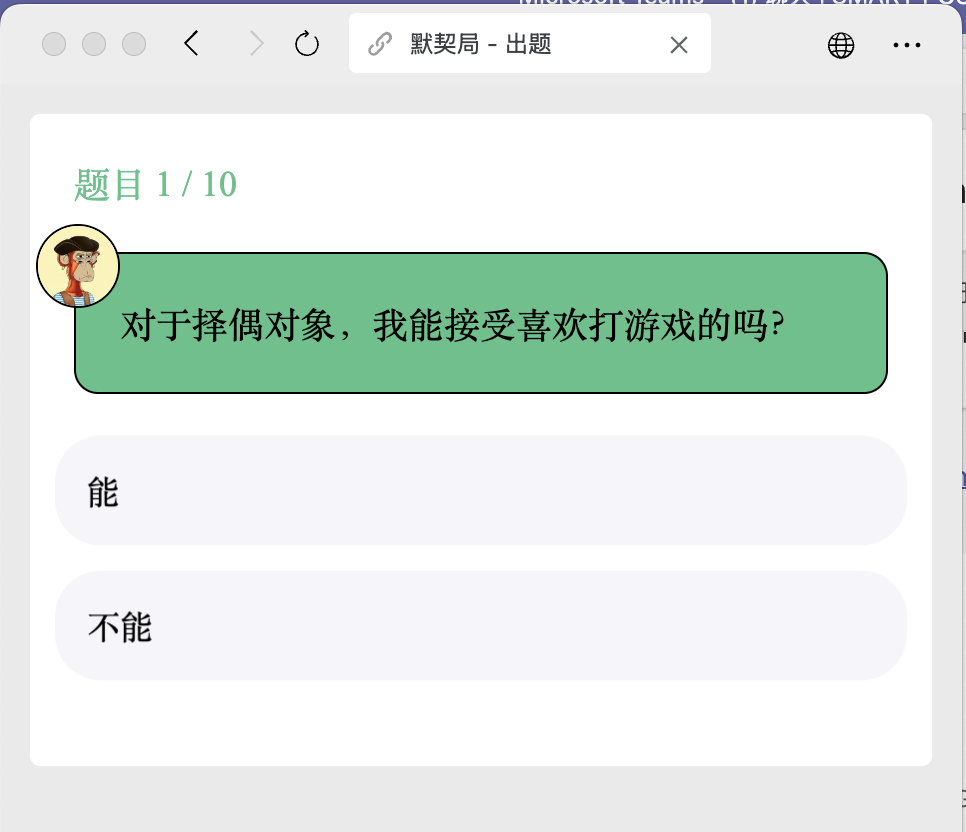
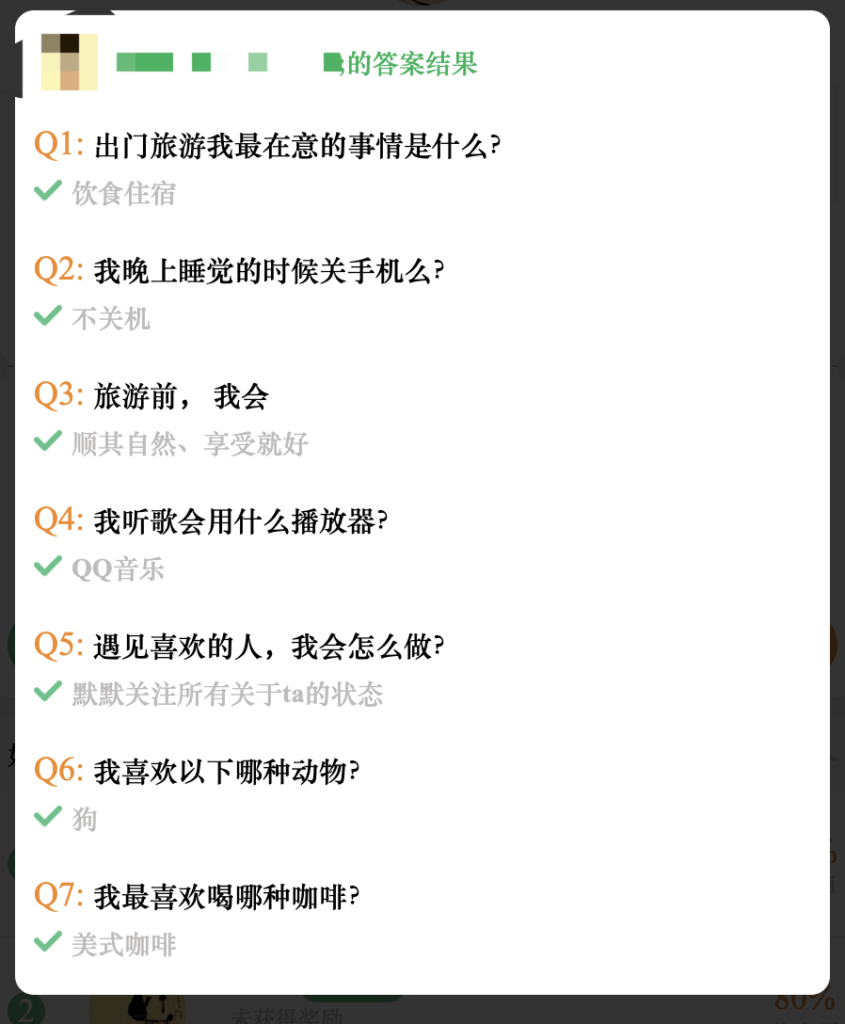
After launching the app (by scanning the QR code), you’ll enter a quiz interface with a total of 10 questions. A correct rate of 80% or higher will earn you a reward. The interface is as shown in the image below, and it can only be opened within the WeChat environment:
Infiltration Strategy
In penetration testing for Q&A functionalities, a common logic issue arises when the server sends questions and answers back to the client, leading to problematic validation and score submissions. Various factors can cause this, from design flaws to business requirements:
- Q&A Type: Given the unstable network environment of end users, the business decided to return the validation logic to the client for a better user experience.
- Scoring Type: Transmitting every step and score in real-time poses a significant challenge for backend architecture. Instead, it’s more efficient for the frontend to calculate a total score and send it to the backend.
- Level-based Games: Similar to “Sheep, Sheep,” where users can replay uploaded results, leading to the potential for multiple completions.
Practical Application
Traffic Hijacking via WeChat Browser
Since it must be accessed through WeChat’s browser, traditional methods of hijacking traffic by setting up a proxy in the browser are no longer feasible, requiring alternative approaches. The core logic is to accurately capture the traffic from the WeChat browser and ensure that the relevant intermediary CA certificates are trusted by the system.
There are many tutorials online, most of which use proxifier along with Burp or Fiddler, so I won’t delve deeper into the step-by-step instructions here. Personally, I prefer using the combination of Surge and Yakit, and here’s a general setup:
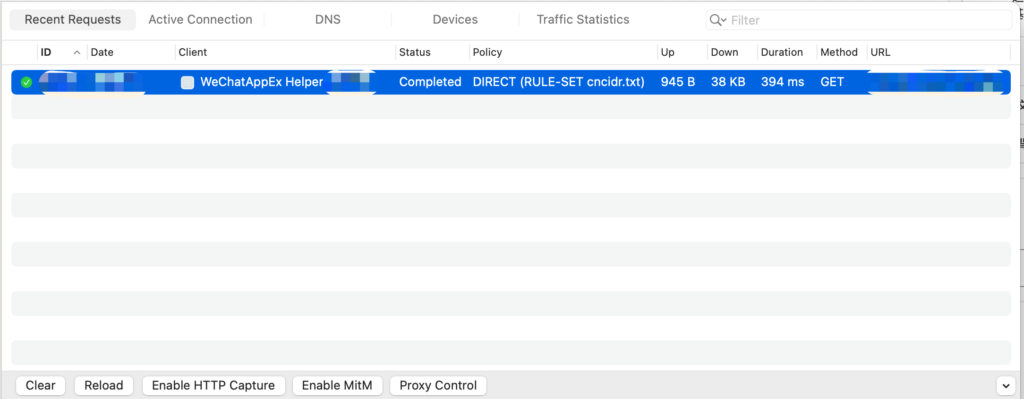
Activate Surge’s enhanced mode and have the WeChat browser access the relevant website, then find the corresponding traffic information in the Dashboard:
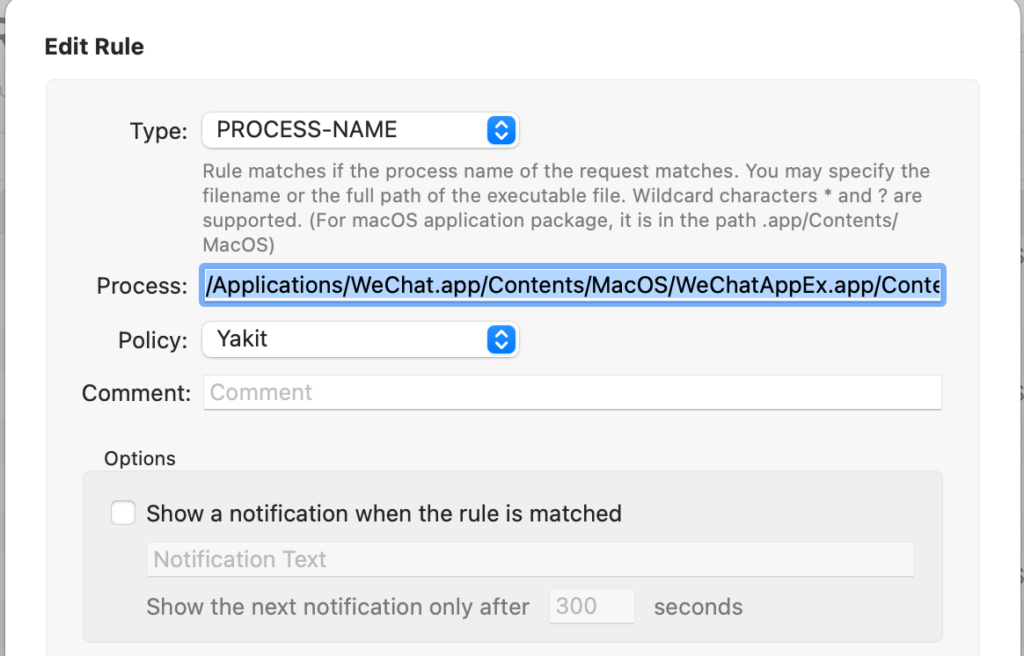
Set up rules for the identified process, in this example, it’s the WechatAppEx Helper process, and apply the Yakit strategy to this process’s traffic:
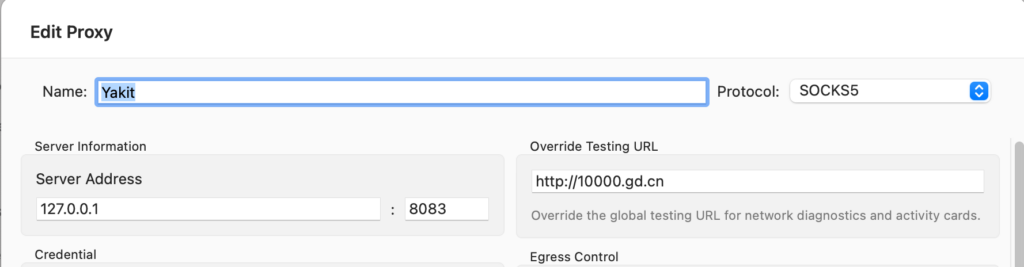
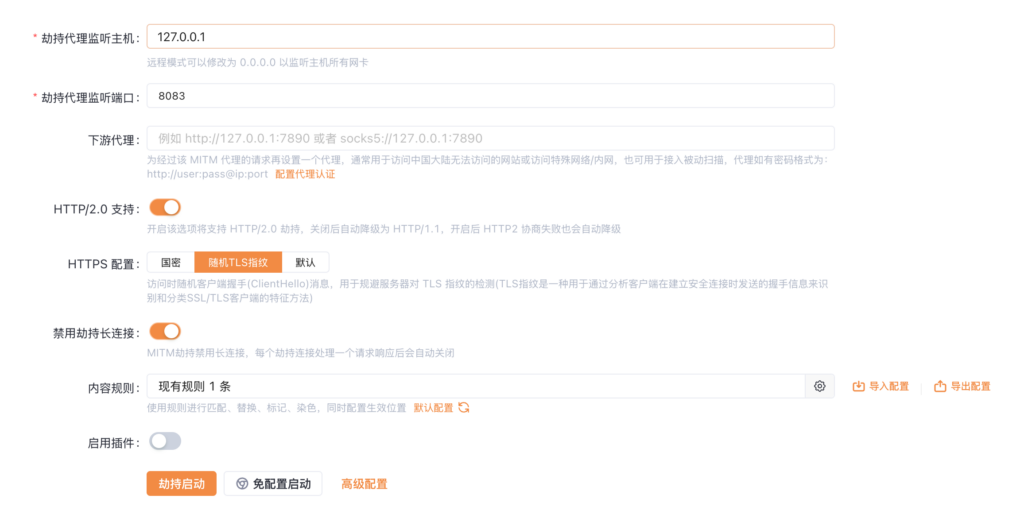
The Yakit strategy needs to match the listening port for the MITM, which I’ve set to 8083:
Yakit’s MITM settings:
Code Review
After completing the above steps, re-enter the quiz page and you’ll see that the traffic has been successfully captured and is now in the Yakit software:
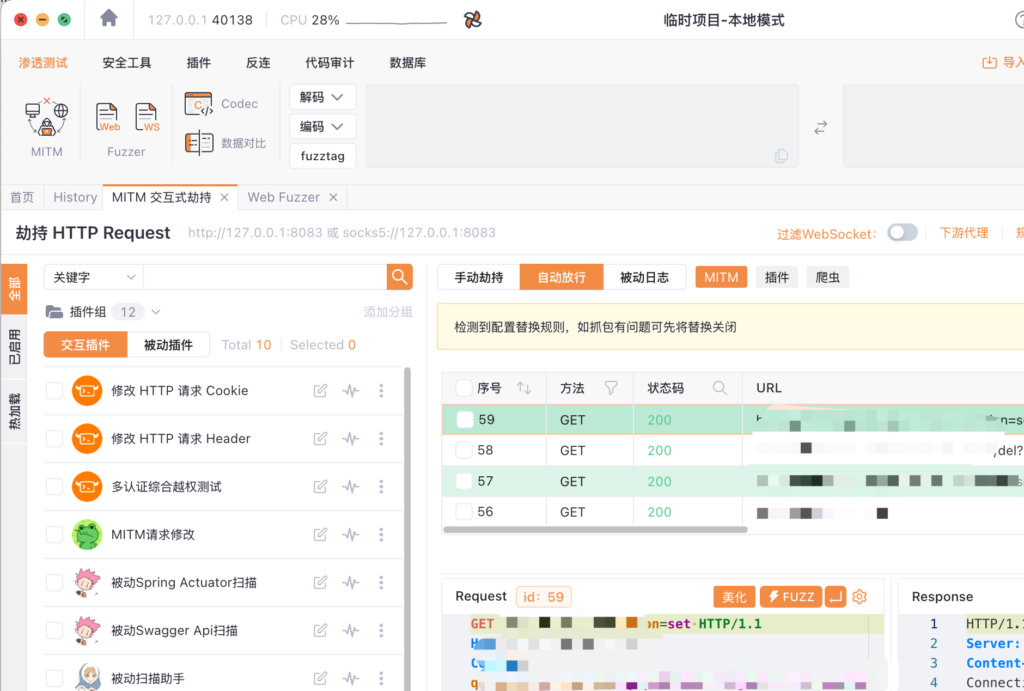
The next steps are straightforward. Just like using Burp, search the traffic for characters included in the displayed quiz questions to locate the relevant code. Generally, the logic will be found in the JavaScript code. Note that if the text is in Chinese, you should also consider searching for escaped characters.
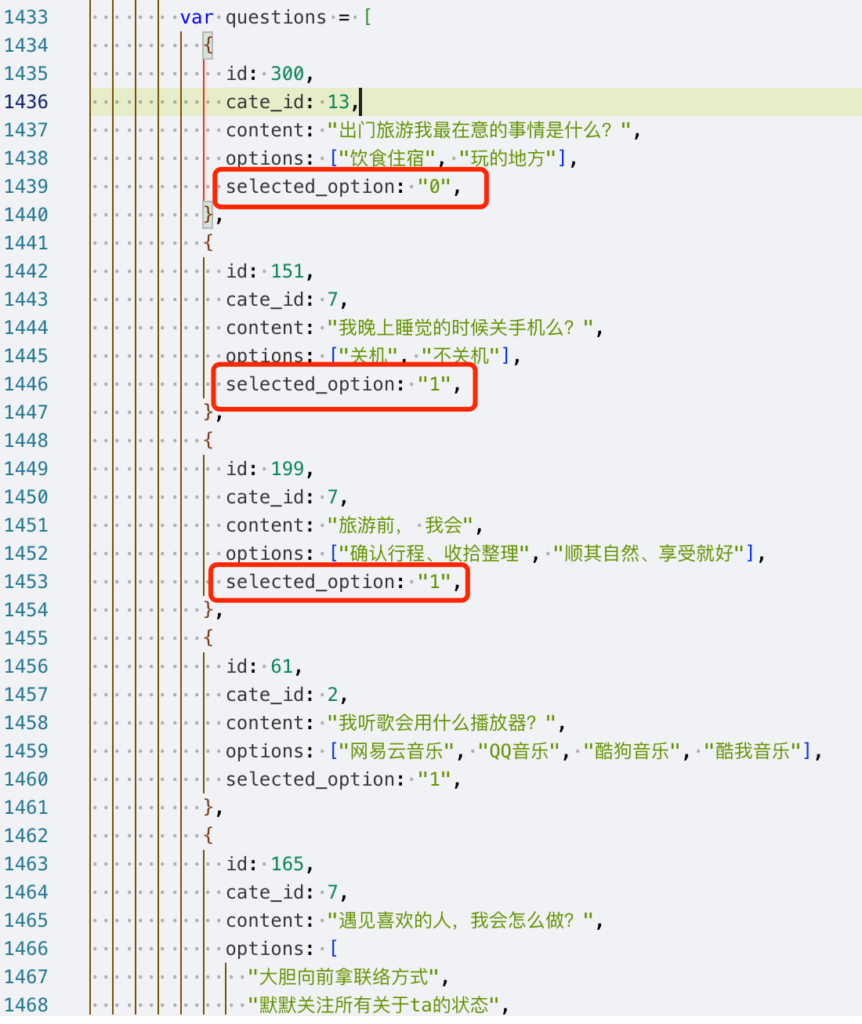
In this case, as the project was rather simple, the developers embedded the script directly on the page, making it easy to trace back the questions and answers. As shown in the code below, the array starts from 0, and you can retrieve each question’s answers using selected_option and options.
The final answers were also quite predictable…
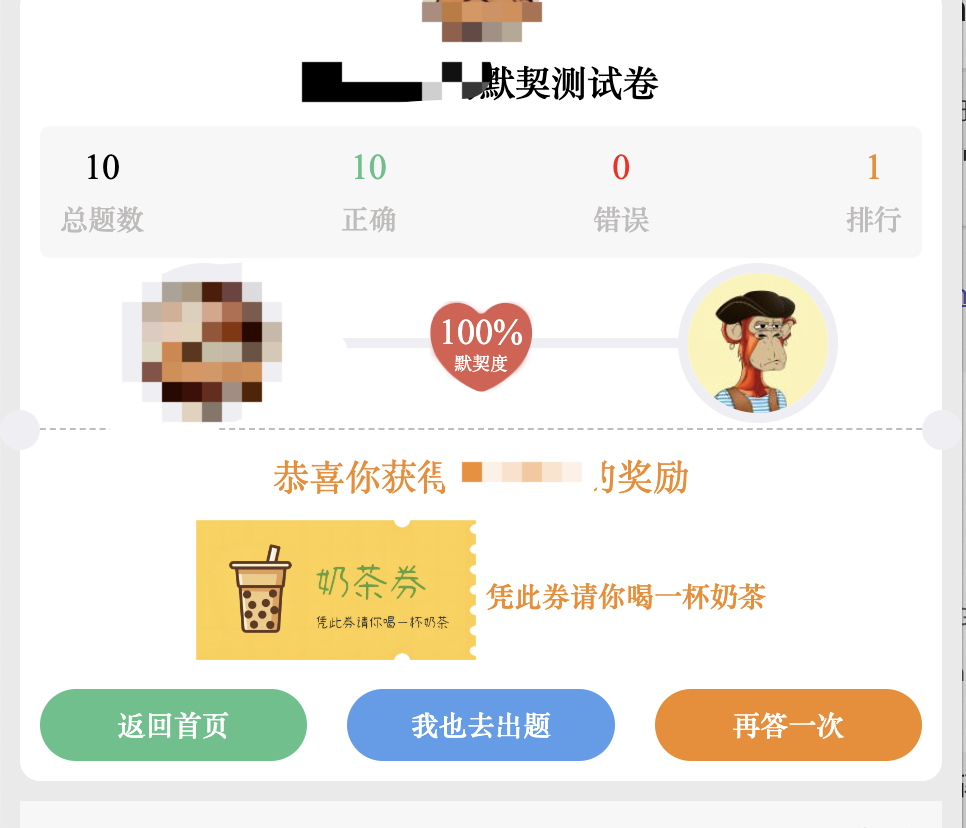
I successfully earned my first cup of milk tea today:

Follow-Up
For Q&A and game-type business scenarios, most solutions tend to be similar. Reflecting on the development logic from both developers and business personnel in these situations can lead to delightful surprises during penetration testing.
After completing the quiz, I found that the final screen has an option where you can pay $1.90 to view all the answers and see other people’s responses…
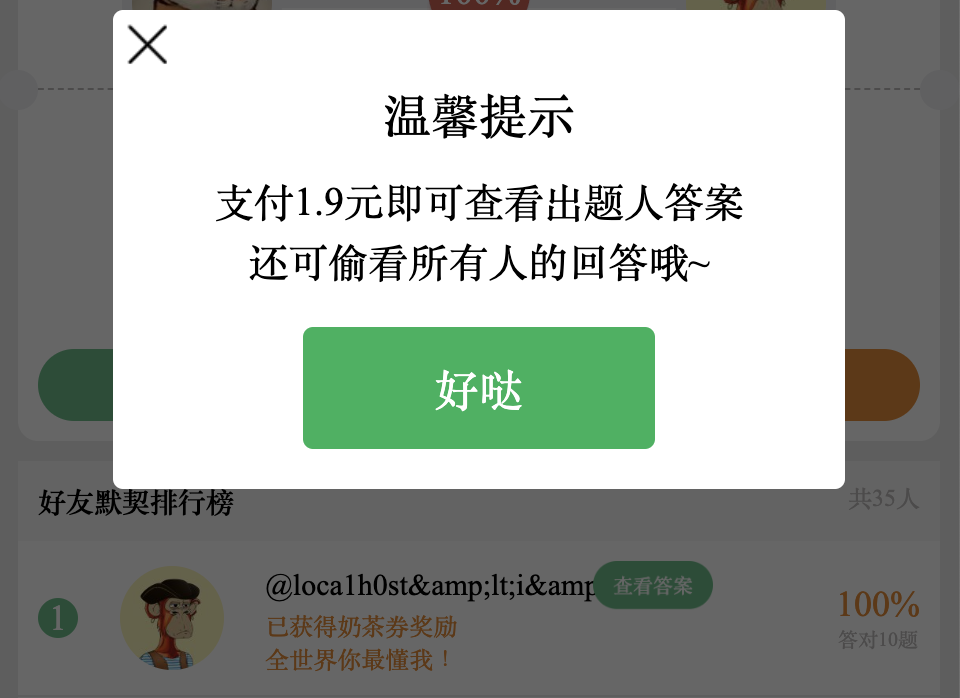
Using the same logic, I explored the business logic in the JavaScript. Although I didn’t find a way to get it for free, I discovered that the developer simply implemented an unlock_status flag to indicate whether the payment was successful:
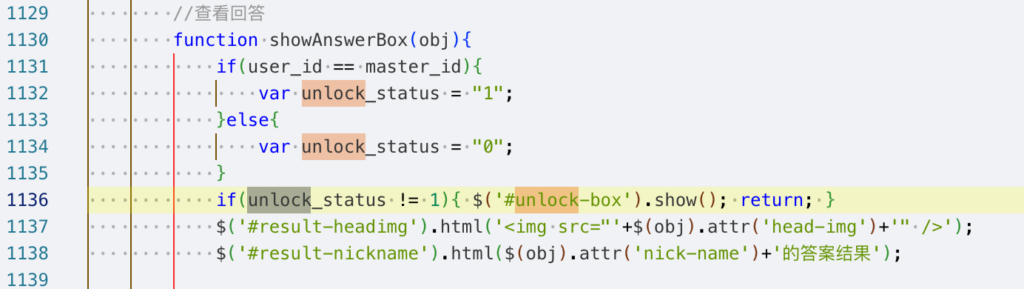
In a traditional penetration test, you could directly bypass this restriction by manipulating the unlock_status in the console. However, due to the limitations of WeChat’s browser, we can’t open the console. Therefore, we can consider using Yakit to modify the response package for bypassing. Adjusting field values or ensuring that conditions are always met can work.
We can inspect the code above to locate user_id and set its value to always equal master_id to bypass the restriction:
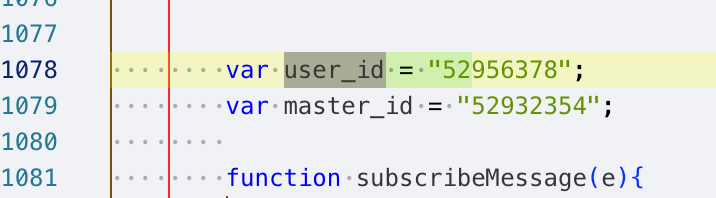
Add a rule in Yakit:
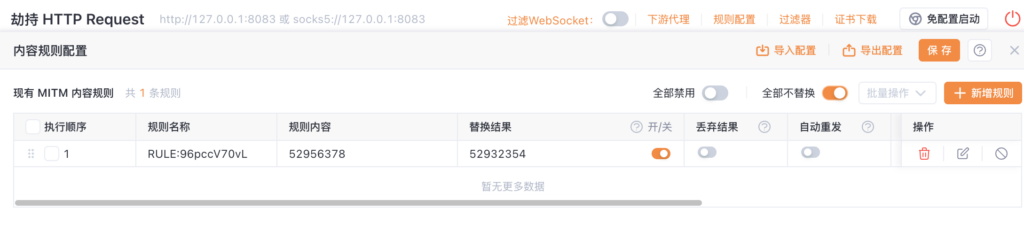
Refresh the page again, and you can bypass the payment:
The MITM rules might be a bit too broad and hard to understand. You could use an interactive plugin or write a MITM plugin yourself for more precise control, which would also work:

Leave a Reply